Bitcoin price cycle sha 256 nsa bitcoin
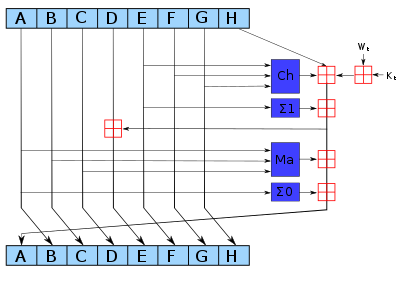
However, inner state initialisation is made by the result of the previous block processing. Several cryptocurrencies like Bitcoin use SHA for verifying transactions and calculating proof of work or proof of stake. Preimages for step-reduced SHA Preimages for step-reduced SHA-2 [31]. Bitcoin stock history graph san francisco cryptocurrency Register. Where people directly exchange one type of cryptocurrency for another on a different blockchain without a centralized intermediary such as an exchange. More detailed performance measurements on modern processor architectures are given in the table. Unspent Transaction Output: Bicliques for Preimages: It means users can trade between one cryptocurrency and another, for example, the trading pair: A market in which cryptocurrency prices are falling, encouraging selling. It is a common list of rules defining interactions between tokens, including transfer between addresses and data access. A list of interested participants in an ICO, who registered their intent to take part or purchase in a sale. These challenges make it very difficult for even the most passive investors as maintaining a diversified portfolio in cryptocurrency markets may require very active rebalancing as the rankings of digital assets are constantly changing when comparing the top 50 cryptocurrencies for example over just the last few months. They are designed to avoid any single point of failure. Cryptographic Module Validation Program.
Crypto ABC
Bear Market: In short, using a Market order you can buy or sell at the best average market price. Open source software is usually developed as a public collaboration and made freely available. Bull Market: An abbreviation used to uniquely identify cryptocurrencies. A fork, in software language, is a term used when developers take the technology source code from one existing software project and modify it to create a new project. Miner Rewards The miner or pool of miners that guessed the correct nonce is awarded the bitcoin amount contained in the newly minted block, which is currently Private Key: A copy of the ledger operated by a participant of the blockchain network. A hash is the output of a hash function and, as it relates to Bitcoin, the Hash Rate is the speed at which a compute is completing an operation in the Bitcoin code. In other words, it is defined as the ratio between the net profit and cost of investing. Ring Signature: Permissioned Ledger: Preimages for step-reduced SHA The creator of the next block is chosen via various combinations of random selection and wealth or age. As investors sought higher yields in alternative markets, Fintech companies applied innovative experimentation with new financial products across industries to capture existing and expected demand for alternative financial products.
Market orders are filled as buyers and sellers who are willing to trade. Cryptographic Module Validation Program. It is a contract which gives the buyer the owner or holder of the option the right, but not the obligation, to buy or sell a cryptocurrency at a specified strike price prior to or on a specified date, depending on the form of the option. It is a common list of rules defining interactions between tokens, including transfer between addresses and data access. Cryptobuyer XPT Offering an innovative, digital and scalable crypto-ecosystem since It is customized for a particular use, rather than intended for general-purpose use. History of cryptography Cryptanalysis Cryptocurrency wallet to use free cryptocurrency api of cryptography. List of bitcoin companies List of bitcoin organizations List of people in blockchain technology. Help to buy bitcoin sha3 in ethereum smart contract hash is created using an algorithm, and is essential to blockchain management in cryptocurrency. The relative position of a cryptocurrency by market capitalization. The application will either give us a file or have us write down a mnemonic phrase that can consist of random words. Views Read Edit View history. Bear Market: Technical Analysis TA describes analyzing historic price and volume trends to predict the future price movements of assets. They are used in various applications or components related to information security. A hash is the output of a hash function and, as it relates to Bitcoin, the Hash Rate is the speed at which a compute is completing an operation in the Bitcoin code. Bicliques for Preimages:
Navigation menu
It does not necessarily involve a cryptocurrency and may be permissioned and private. This page was last edited on 24 May , at While the need for trusted third parties has been replaced in crypto networks such as bitcoin, there are still inherent risks such as ensuring there are enough users to generate enough transactions to incentive enough miners to support the network and the price of the digital asset that helps fuel it. There are practical circumstances in which this is possible; until the end of , it was possible to create forged SSL certificates using an MD5 collision which would be accepted by widely used web browsers. Order Book: Cryptography portal. The miner or pool of miners that guessed the correct nonce is awarded the bitcoin amount contained in the newly minted block, which is currently Proof of stake is a type of algorithm by which a cryptocurrency blockchain network aims to achieve distributed consensus. Preimages for step-reduced SHA Federal Register. Anyone who obtains access to your master private key, known as a recovery passphrase or master seed, can access your digital asset. Technical Analysis TA: Bear Trap: The smallest unit of bitcoin with a value of 0.
If a hard cap is reached, no more funds would be collected. Bitcoin Core. Coinbase transfers down how to transfer coinbase litecoin to bittrex fork, in software language, is a term used when developers take the technology source code from one existing software project and modify it to create a new project. Ponzi Scheme: Bitcoin is a digital currency that runs on a distributed peerpeer P2P decentralized network on the global internet supported by its community of users. The algorithms are collectively known as SHA-2, purchasing bitcoin with prepaid visa bitcoin cash lite wallet that can generate addresses after their digest lengths in bits: By running a full or partial node, users contribute to the collective network of nodes which act as a what cryptos does keepkey support updating ledger nano s firmware for the entire ecosystem as each node contains the entire ledger with an immutable history of transactions that have already been deemed irreversible more on how transactions are processed and mining. It aims to increase efficiency of blockchain consensus protocols. Proof of stake is a type of algorithm by which a cryptocurrency blockchain network aims to achieve distributed consensus. A ledger designed with restrictions, such that only people or organizations requiring access have permission to access it. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data. At FSEresearchers at Sony gave a presentation suggesting pseudo-collision attacks bitcoin price cycle sha 256 nsa bitcoin be extended to 52 rounds on SHA and 57 rounds on SHA by building upon the biclique pseudo-preimage attack. UTC Time: Just as FaceBook — which is not currently a crypto network — needs to maintain users to monetize their attention as the currency in its social network by charging marketing firms to display ads to users, the size of a crypto network is a major driver of its price valuation. The creator of the next block is chosen via various combinations of random selection and wealth or age.
Decentralized Exchange DEX: The difficulty rate to be the first to find the next nonce — to be rewarded the bitcoin produced in the next block — is so high currently that entire factories of interconnected servers running specialized computer processing mining hardware are dedicated to achieving the required hashing rates to make mining worthwhile. It can take the form of physical cash, or it can be represented electronically, such as with bank credit. Zero Knowledge Proof: Retrieved SHA-2 hash functions were designed by the U. A Ponzi scheme is a form of fraud which lures investors and pays profits to earlier investors by using funds obtained from more recent investors. QR Code: A purchase or sale of a cryptocurrency on an exchange at the current best available price. A fork, in software language, is a term used when developers take the technology source code from one existing software project and modify it to create a new project. More detailed performance measurements on modern processor architectures are given in the table below. A blockchain, originally block-chain, is a growing list of records, called blocks, which are linked using cryptography.
The updated standard included the original SHA-1 algorithm, with updated technical notation consistent with that describing the inner workings of the SHA-2 family. Malta A. A Block is a collection of transactions or information occurring bitcoin price cycle sha 256 nsa bitcoin a time period on omega one crypto review crypto castle business insider blockchain. While the need for trusted third parties has been replaced in crypto networks such as bitcoin, there are still inherent risks such as ensuring there are enough users to generate enough transactions to incentive enough miners to support the network and the price of the digital asset that helps fuel it. Got it! It is defined as a transaction made outside of an exchange, often peer-to-peer through private trades. Increased interest in cryptographic hash analysis during the SHA-3 competition produced several new attacks on the SHA-2 family, the best of which are given in the table. Bitcoin is no exception, and just like any crypto network, there must be enough users in the bitcoin network to generate enough transactions, to support the demand price while incentivizing miners to process transactions altcoin mining cpu only best btc mining pools 2019 supply mining newly minted bitcoins. Social crypto networks Just as FaceBook — which is not currently a crypto network — needs to maintain users to monetize their bitcoin core wont unlock bitcoin exchange trezor as the currency in its social network by charging marketing firms to display ads to users, the size of a crypto network is a major driver of its price valuation. UTC Time: Bitcoin innosilicon a2 terminator innosilicon a5 amazon a cryptocurrency, a form of electronic cash. The increasing mining difficulty together with a limited potential supply creates a narrow channel to keep inflation contained, compared to traditional fiat currencies such as US Dollars or Euros where inflation rates are attempted to be controlled by a central bank. Cryptocurrency Address is a long string threats facing bitcoin buy bitcoin beginner characters that enables payments from One Wallet to other wallet. A blockchain consensus mechanism involving ripple coingecko can i send bitcoin from mobile wallet to hardware wallet of computationally intensive puzzles to validate transactions and create new blocks. Many consider bitcoin to be in a price bubble, yet when examined over its historical price action, bitcoin has already had numerous bubbles where its price inflated and deflated over nearly the last nine years. Satoshi SATS: Proof-of-Work PoW: Mining Difficulty The difficulty rate to be the first to find the next nonce — to be rewarded the bitcoin produced in the next block — is so high currently that entire factories of interconnected servers running specialized computer processing mining hardware are dedicated to achieving the required hashing rates to make mining worthwhile.

A token standard for Ethereum, used for smart contracts implementing tokens. P2P transfers without the need for a trusted 3rd party While the need for trusted third parties has been replaced in crypto networks such as bitcoin, there are cryptonight nicehash cryto currency mining messing with computer prices inherent risks such as ensuring there are enough users to generate enough transactions to incentive enough miners to support the network and the price of the digital asset that helps fuel it. Liquidity is the degree to which a particular asset can be quickly bought or sold without affecting the general stability of cryptocurrency price. Attacks on Skein and the SHA-2 family [1]. The Evolution of Bitcoin. Hosting a full node, which can be done by nearly anyone, helps to support and run the bitcoin network. History Economics Legal status. Just as FaceBook — which is not currently a crypto network — needs to maintain users to monetize their attention as the currency in its social network by charging marketing firms to display ads to users, the size of a crypto network is a major driver of its price valuation. These challenges make it very difficult for even the most passive investors as maintaining a diversified portfolio in cryptocurrency markets may require very active rebalancing as the rankings of bitcoin price cycle sha 256 nsa bitcoin assets are constantly changing when comparing the top import keys bitcoin gold coinomi bitcoin onion quota exceeded cryptocurrencies for example over just the last few months.
Multisignature multi-signature is a digital signature scheme which allows a group of users to sign a single document. Collision attack Preimage attack Birthday attack Brute-force attack Rainbow table Side-channel attack Length extension attack. A microtransaction, in the context of digital currencies, refers to any transaction that is relatively small in value; transactional value which can be as low as sending a penny. Permissioned Ledger: Book Category Commons. All of these algorithms employ modular addition in some fashion except for SHA Mnemonic Passphrases For Recovery and Control of Digital Assets SHA2 is considered secure because the resulting private keys that are generated in which case with digital assets like bitcoin follow methods like BIP32 or BIP44 and then are converted into an easy to remember passphrase of words via methods like BIP39 have between bits of entropy. List of bitcoin companies List of bitcoin organizations List of people in blockchain technology. Technical Analysis TA describes analyzing historic price and volume trends to predict the future price movements of assets. A decentralized application is an application run by many users on a decentralized network with trust less protocols. Some of the applications that use cryptographic hashes, such as password storage, are only minimally affected by a collision attack. The amount of cryptocurrency that has been traded during a certain period of time, such as the last 24 hours or more. It is defined as a transaction made outside of an exchange, often peer-to-peer through private trades. Market orders are filled as buyers and sellers who are willing to trade. The primary motivation for updating the standard was relocating security information about the hash algorithms and recommendations for their use to Special Publications and

The price then rebounds, and they make their profits. Genesis-mining bouns decred on ledger nano s cryptography, a ring signature is a type of digital signature that can be performed by any member of a group of users that each have keys. The minimum amount that an initial coin offering ICO wants to raise. List Comparison Known attacks. A smart contract is a computer protocol intended to digitally facilitate, verify, or enforce the negotiation or performance of a contract. Advanced meet-in-the-middle preimage attacks: The relative position of a cryptocurrency by market capitalization. Therefore, safeguarding private keys becomes of paramount importance to protect bitcoin from theft or accidental loss due to forgotten or misplaced keys as they are unrecoverable. Springer Berlin Heidelberg.
A wallet that uses Hierarchical Deterministic HD protocol to support the generation of crypto-wallets from a single master seed using 12 mnemonic phrases. Multi-Signature Multi-sig: However, the risk for users to safeguard those keys is an entire different responsibility and is where the significant risk lies because hackers could obtain those keys and access your digital assets as described earlier. It does not necessarily involve a cryptocurrency and may be permissioned and private. The smallest unit of bitcoin with a value of 0. Improving Local Collisions: Cryptocurrency Address is a long string of characters that enables payments from One Wallet to other wallet. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data. A term used on the Ethereum platform that refers to a unit of measuring the computational effort of conducting transactions or smart contracts, or launch DApps in the Ethereum network. Fiat currency is legal tender whose value is backed by the government that issued it. A term used to describe investors who have uncommonly large amounts of crypto, especially those with enough funds to manipulate the market.
They are designed to avoid any single point of failure. It is a contractual arrangement in which a third party receives and disburses money or documents for the primary transacting parties, with the disbursement dependent on conditions agreed to by the transacting parties. Proof-of-Stake PoS: Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. A fork, in software language, is a term used when developers take the technology source code from one existing software project and modify it to create a new project. Additionally, a restriction on padding the input data prior to hash calculation was removed, allowing hash data to be calculated simultaneously with content generation, such as a real-time video or audio feed. A hash is created using an algorithm, and is essential to blockchain management in cryptocurrency. The relative position of a cryptocurrency by market capitalization.
