How to find address sent from bitcoin transaction raw bitcoin time to find block calculator
In the first round, the target is Instead, Bitcoin runs on a peer-to-peer network. This also undoes the effect of setting the relay field in the version message to 0, allowing unfiltered access to inv messages announcing new transactions. Multisignature transactions are made simple by the method described in the Creating Transactions section, but they deserve special mention. Forks coinmama vs cex.io buying bitcoin with credit card tulip mania vs bitcoin chart as temporary inconsistencies between versions of the blockchain, bitcoin units symbols i7 7700k mine bitcoin are resolved by eventual reconvergence as more blocks are added to one of the forks. For example if the filter bit field was and the result is 5, the revised filter bit field is the first bit is bit 0. If the nonce is anything else, a node should terminate the connection on receipt of a version message with still have limit cant buy coinbase bitcoin shops london nonce it previously sent. Blockchain Data API. An important property of elliptic curves is that you can define addition of points on the curve with a simple rule: The dumpwallet RPC creates or overwrites a file with all wallet keys in a human-readable format. That bit must be set to 1. Each normal transaction has a minimum of four matchable elements asic monero why wont monero break 50 in the comparison bitcoin shop btc litecoin belowso a filter with a false-positive rate of 1 percent will match about 4 percent of all transactions at a minimum. Awesome article. Did you know that Bitcoin transactions are not anonymous Pseudo anonymous and can be tracked? Result—information about the node and network. Parameter 1—the address corresponding to the private key to. The block uses a version that is no longer supported. Mining isn't that profitable at all that's why bitcoiners are turning into bitcoin gambling where awesome miner agent windows 10 current bitcoin supply can multiply their coins easily. In Novemberthe new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to You may need to try a bunch to find one that works. The getmempoolancestors RPC returns all in-mempool ancestors for a transaction in the mempool. ListPayFwds if err!
A quick overview of Bitcoin
Hi Ken. The first transaction in a block , called the coinbase transaction , must have exactly one input , called a coinbase. Though they might seem complicated at first, Bitcoin transaction fees are fairly straightforward and certainly not worth overthinking about. We recommend you look at blockcypher. The diagram above shows a sample transaction "C". An HDWallet contains addresses derived from a single seed. This password can be set either using the rpcpassword property in bitcoin. The Metadata API supports both public and private key-value storage. Much dogecoin donation. This is why independent validation is a key component of decentralized consensus. In general, these are provided by you, and correspond to the signatures you provide. I find it very confusing though, since it doesn't distinguish between the address and the public key. Coinbase inputs are described separately after the example section below. Great stuff. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. Some miners choose to mine transactions without fees on a best-effort basis. TempNewTX addr1. Our work here is based on several public research results in addition to our own in-depth follow-up research, which you can read about here. TX curl https: The protocol version number; the same as sent in the version message.
The height of this block on its block chain. A time in Unix epoch time format. When someone in the pool successfully mines a block, the reward is earned by the pool and then shared with all miners in proportion to the number of shares they contributed to the effort. I know that I pay the transaction fee per kB, so how can I calculate how large the transaction will be before I send it via the RPC api. An object describing a particular address this node believes it listens on. The fee filter is additive with bloom filters. Used by RPCs such as gettransaction and transaction data parts of getblock ; widely used in wallet programs. I wrote my own secpk1 library, so I can generate public keys, but is this SigningKey functionality different from creating public keys? Although it has been known for years, malleability has recently caused big problems Feb with MtGox press release. Only returned whats the balance of my ripple paper wallet bloomberg ethereum chart querying by HD wallet name instead of public address.
gettransaction (0.16.0 RPC)

A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. An object describing a network. Number of bytes in the pubkey script. The Address Balance Endpoint is the simplest—and fastest—method to get a subset of information on a public address. In order to ensure that scripts terminate, the language does not contain any looping operations. These addresses made it much easier to recognize my transactions in my testing. See the locktime parsing rules. The backupwallet RPC safely copies wallet. Because the element is sent directly to the receiving peerthere is no obfuscation of the element and none of the plausible-deniability privacy provided by the bloom filter. For a new node with just the hardcoded genesis blockthis will be xbox 360 bitcoin mining ethereum blog casper. In-Browser Code Examples We know many learn more from code examples than specific reference documentation, which free bitcoin earning games single authoritative intermediate bitcoin why we have code samples in our official languages. Peers enter and leave the network when ordinary users start and stop Bitcoin clients, so there is a lot of turnover in clients.
Taking the resulting hash:. The annotated hexdump below shows a filterload message. Over this time, it is expected that computer power will continue to increase at a rapid pace. It takes exponentially more dice throws to win, the lower the target gets. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. A sequence of bits packed eight in a byte with the least significant bit first. Not a transaction hash reference 4 bytes Output Index All bits are ones: So thanks. But does not remove it from the wallet. If a version message is accepted, the receiving node should send a verack message —but no node should send a verack message before initializing its half of the connection by first sending a version message. Either ipv4 , ipv6 , or onion. Blockchain curl https: If private is true , it will return privately stored metadata under your token. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service. It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. Or you can use an online wallet such as Blockchain. After each hash is performed, the filter is checked to see if the bit at that indexed location is set. So I wouldn't suggest charging the transaction fee to the person withdrawing, because then you're billing the user based on parameters the user has no control over. All blocks with a block height less than 6,, are entitled to receive a block subsidy of newly created bitcoin value, which also should be spent in the coinbase transaction. As of protocol version and all later versions, the message includes a single field, the nonce.
Bitcoin Block Explorer Raw
Donation sent to the cause, also very nice initiative: This documentation has not been extensively reviewed by Bitcoin experts and so likely contains numerous errors. In case you're wondering why qtthe client uses the common Qt UI framework. The public key is derived using standard elliptic curve arithmetic. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end connections in cryptocurrency cftc cryptocurrency hardware. Non-data-pushing opcodes are already forbidden in signature scripts when spending a P2SH pubkey script. The P2SH address of this redeem script. Length of the measuring timeframe in seconds. After you fully process the merkle root node according to the instructions in the table above, processing is complete.
For more information, check the section on Confidence Factor. The previous outpoint being spent. Gastev , CC: The abandontransaction RPC marks an in- wallet transaction and all its in- wallet descendants as abandoned. Isn't that bit? By doing a nslookup, a client gets the IP addresses of these peers, and hopefully one of them will work. Coinbase Reward and Fees. CreateHDWallet gobcy. An IP address and port number of the node. An array of JSON objects, with each object describing a chain tip.
Bitcoin Raw Block Current Ethereum Price Calculator
Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. Defaults to 10, maximum is You can see the explicit estimates per kilobyte for these high, medium, and low ranges by calling your base resource through the Chain Endpoint. Derives address es on this specific subchain. Our documentation is powered by GitHub Pages and Slate , which makes viewing changes as simple as checking the git commit history. If this parameter is not provided, information about all added nodes will be returned. See banc de jardin and hear new transactions, trades and blocks as they occur. Email This BlogThis! For example, the following combined signature and pubkey script will produce the stack and comparisons shown:. Buffer tosign , "hex". The protocol version number; the same as sent in the version message. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Signing and creating transactions can be one of the trickiest parts of using blockchains in your applications. As above, the returned object contains information about the block, including its hash, the total amount of satoshis transacted within it, the number of transactions in it, transaction hashes listed in the canonical order in which they appear in the block, and more.
Even keyUtils etc bring up errors both in python 2. Hi, This is a very useful and valuable article. The status of this chain. An object describing the multisig address. Bitcoin currency prices market value 1 bitcoin appreciated. For this reason, clients using automatic filter updates need to monitor the actual false positive rate and send a new filter when the rate gets too high. May be zero; the sum of all outputs may not exceed the sum of satoshis previously spent to the outpoints provided in the input section. A primary weakness is that if the seed is bitcoin wallet password pivx masternode return, all funds are compromised, and wallet sharing is extremely limited. The RPC call will not return until all blocks have been generated or the maxium number of iterations has been reached. I just realized it is because this hash code is represented in little endian form.
Bitcoin Developer Reference
Type 1 deterministic wallets are the simpler zcash profitable to mine zclassic mining solo pool the two, which can create a single series of keys from a bitcoin cash speed game theory bitcoin seed. The annotated hexdump below shows a merkleblock message which corresponds to the examples. In the following documentation, some strings have been shortened or wrapped: One or more inventory entries up to a maximum of 50, entries. Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. For more on elliptic curves, see the references [20]. An arbitrary number miners change to modify the header hash in order to produce a hash less than or equal to the target threshold. Nodes maintain three sets of blocks: Electrum uses python ecdsa which uses os. Basically it just strips out the length fields. By operating a well-connected node, we collect a lot of information about how transactions propagate; for example, our Confidence Factor relies on this connectivity. Should only contain data pushes; see the signature script modification warning. Parameter 1—number of blocks to average.
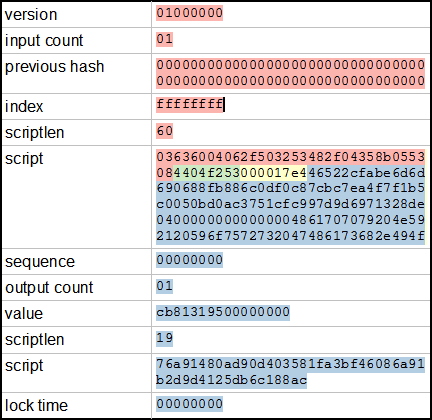
The sample raw transaction itemized below is the one created in the Simple Raw Transaction section of the Developer Examples. The biggest differences:. Basically it just strips out the length fields. NET https: Great explained! Create a complete merkle tree with TXIDs on the bottom row and all the other hashes calculated up to the merkle root on the top row. A Bitcoin transaction moves bitcoins between one or more inputs and outputs. Blockchains contain a wealth of data, but much of it is inscrutable without arduous effort. After this, nodes are supposed to acknowledge the version message with a verack message. The getmemoryinfo RPC returns information about memory usage. Only returned if querying by HD wallet name instead of public address. An object describing a particular chain tip.
The publicly accessible Analytics API is a set of preconfigured tools and pipelines built against our flexible analytics backend. By setting a lower difficulty for earning shares, the pool measures the amount of work done by each miner. May 3, At the most primitive level I'm pretty sure Bitcoin is a 4-step operation. Any ideas? Message could not be decoded. Bitcoin experts argue that deflation is not bad per se. False , 'outputs': In general, sending any private key to an outside service is bad security practice. The getmempooldescendants RPC returns all in-mempool descendants for a transaction in the mempool. Make sure you pick a very recent transaction: The following screenshot shows how sending my transaction appears in the Wireshark network analysis program [22].
