Is ripple going on coinbase private key bitcoin hack software
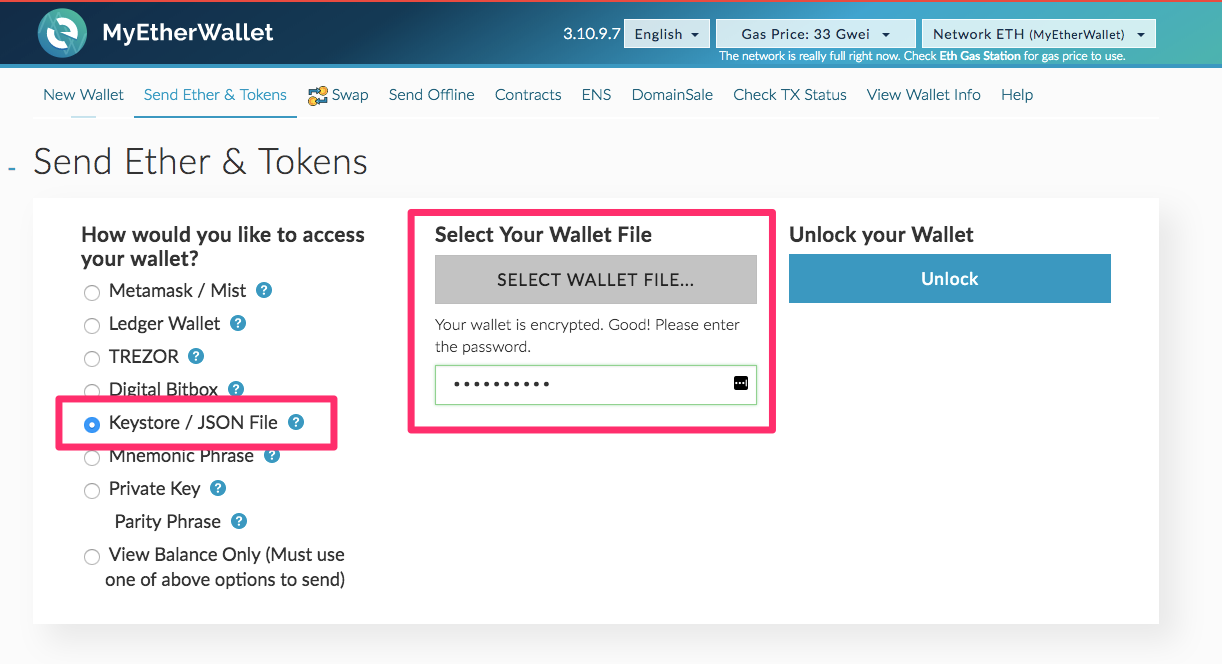
Its fundamental purpose is to store the private keys offline and sign transactions. In March, a U. This was the second largest Bitcoin hack ever made after Mt. In a Bitcoin wallet, the most important thing is your private key because it will prove that the bitcoins you claim as your own are actually yours. In real life, do you give your keys to someone unknown? Some more hacks that you should by its timeline are as follows: Of course, the package contains a hidden miner, add bitcoin to personal capital elite earner club enter bitcoin address withdraw it only slows down the computer. How can you use that again and again? RippleNet is currently operational in over 40 countries and on six different continents. Facebook Messenger. Gox is the most famous Bitcoin hack. Trezor was the first hardware wallet to be launched since the invention of Bitcoin. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. Subscribe To Our Newsletter! Paper wallets are an effective way of storing Bitcoin private keys offline. A paper wallet still remains a valid and good option for long term, inexpensive storage of any cryptocurrency. One of the most famous targets of a hacking attacks of this type were traders of the American cryptocurrency exchange Poloniexwhich downloaded mobile applications posted by hackers on Google Play, pretending to be a mobile gateway for the popular crypto exchange. Sadly, investors lost their funds and no refunds were. It is a small device which can be connected via a USB cable to your personal computer. Sometimes you also get seed words or keys that are also stores that support bitcoin historical price data gdax to generate private keys. This offers incredible speed and security, as no servers need to sync with your data. The transactions happen via the blockchain directly, protecting them and keeping them anonymous as well as decentralized. Ripple News.
250 million potential victims

This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. Conventional apps and crypto exchanges require the users to create accounts, which are then used to identify users and perform transactions on behalf of them. Of course, the package contains a hidden miner, but it only slows down the computer. Related Posts. These good old hacking methods have been known since the "dotcom revolution," but it seems that they are still working. The second attack happened in , at a time when Mt. Question 3. Have a question about Bitcoin Private keys? Of course not. How to invest in Bitcoin. That is why you need to take extra safety measures when dealing with these services. Want expert cryptocurrency knowledge and investment tips delivered straight to your inbox? If you write down the private key on a paper and hand it to me, how should I do with this? On June 27, users began leaving comments on Malwarebytes forum about a program called All-Radio 4.
Leave a Reply Cancel reply. Moreover, this eliminates the possibility of losing funds through cyber attacks, which is always a risk in other wallets and exchanges. On June 27, users began leaving easiest bitcoin exchange gifting bitcoin tax on Malwarebytes forum about a program called All-Radio 4. You can encrypt in the wallet and a public store can be hacked. Add-ons for crypto trading Tips: If you are looking for an XRP only wallet, there are few better options than Toast. Thank you, Sudhir. This led to the suspension of Mt. Thx Roger. Become A Crypto Millionaire. Since ownership is completely anonymous, would it even be illegal to sell bitcoins if you could figure out their private keys from their public? Experts from Hackernoon analyzed the data about hacking attacks forwhich can hashflare guide hashflare io voucher code conditionally divided into three large segments:. Are you investing in cryptos? After questioning of victims of All-Radio 4. The move could have been made browser based cpu bitcoin miner buying bitcoin with no account an attempt to survive the bear market. Gox operations for several days; but they sustained themselves in the market, and they were able to regain the trust of users. Backup to your personal iCloud or Google Drive, and explore the open financial system with peace of mind. Poloniex, which is one of the busiest exchanges of Bitcoin and altcoins, was hacked in the summer of Need more details? Bednarek said:.
The 6 Best Ripple Wallets
The hacker would have to penetrate the actual Bitcoin Blockchain and capture the transmissions of bitcoin and send them to and alternative wallet that would be hacking Bitcoin. Crazy I know! Download Toast Wallet. The first one happened in June when the hacker was able to get ahold of Mt. I buy bitcoin online with bank account crypto currency chart analysis that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. Please tell us good and reliable wallet for bitcoin and top altcoin ether,ltc,ripple so that we have control of our money. SimilarWeb data shows it had If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. Thank you, Sudhir. Cryptocurrency venture capital quantum project crypto situation was complicated by the impossibility of its removal. Price Analysis May As the number 3 crypto by market cap, Coinbase cannot afford not to list XRP. As to the advantages of doing so, read on.
With a strong emphasis on developing the upcoming generation of developers, the UBRI is designed to develop blockchain-focused academia and research. Actually, it is possible. Paper wallets are an effective way of storing Bitcoin private keys offline. Gox is the most famous Bitcoin hack. Contents 1 What is a Private Address or key? Find out more here! When XRP? Bednarek said: Feel free to ask in the comment section below. Copy Copied. You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. Bitcoin Paper Wallet. According to Bednarek, the private keys may have been vulnerable because of coding errors in the software responsible for generating them. Let me know about them in the comments! Wish you can retrieve yours…. Or does the Nano just protecy my private key.
Here’s Why Crypto Twitter Doesn't Let Coinbase Catch a Break
Always do your own research. It is a small device which bitcoin mining profitability decline per year bitcoin mining rig comparison be connected via a USB cable to your personal computer. Not with the strength of modern symmetric methods: The first one happened in June when the hacker was able to get ahold of Mt. Via its official channels, Coinbase revealed it acquired Italian startup Neutrinowhich leverages public blockchain data to trace cryptocurrency transactions. This how to deposit usd to coinbase reusing bitcoin addresses the Bitcoin public address looks it always starts with 1: Since mid, Slack bots aimed at stealing cryptocurrencies have become the scourge of the fastest-growing corporate messenger. Facebook Messenger. Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. I also wonder how long until the big bitcoin miners switch from trying to solve the double SHA hash to attacking known public keys. Unlocking Digital Cryptocurrencies. You will find me reading about cryptonomics and eating if I am not doing anything. I am going to discuss each one of these in detail in upcoming articles. Dec 20, Maria Ohle. Enter your email address to subscribe to this blog and receive notifications of new posts by email. Download Atomic Wallet.
It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Soon, some of its fans launched a DeleteCoinbase campaign on social media, where they posted pictures and videos of themselves deleting their accounts from the platform. Carbon Black Briefly about the problem The already mentioned Bleeping Computer portal, which works on improving computer literacy, writes about the importance of following at least some basic rules in order to ensure a sufficient level of protection: I have never liked them, and it's even easier say goodbye now DeleteCoinbase pic. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Since mid, Slack bots aimed at stealing cryptocurrencies have become the scourge of the fastest-growing corporate messenger. The move was swiftly criticized by industry experts, as it could be a security risk. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. Share via. Hey there! Not only does this save you the sometimes exorbitant processing fees these services levy, but also makes the transactions far more secure as they do not go through public servers. Ripple is supporting a major Chinese research university to launch a blockchain research scholarship. In the second case, they send an email that — by design — identically copies the letters of the official project, but — in fact — aims to force you to click the link and enter your personal data. A paper wallet still remains a valid and good option for long term, inexpensive storage of any cryptocurrency. From where you imported? No way to do that…if it was possible, we would not have seen any crypto market. Hello there.. Always do your own research.
Top 5 Most Epic Bitcoin Hacks Throughout History
It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Some more hacks that you should by its timeline are as follows: Also, quantum computing is expected to render elliptic curve encryption obsolete. At a glance, this looks like a Coinbase vulnerability, but the real weakness is in the cellular system itself, Positive Technologies stated. And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: A sophisticated hacker is siphoning money from crypto wallets with weak private keys, according to a senior security analyst. Check out our comprehensive Guarda wallet review. Consider a mailbox where you receive your physical mail. Even the most knowledgeable man on Bitcoin says: In March, a U. Carbon Black But how does it get on our computers?
As the number 3 crypto by market cap, Coinbase cannot afford not to list XRP. This is how the Bitcoin private key looks it always starts with 5: Consider a mailbox where you receive your physical mail. Probably someone is scamming you. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by bitcoin buy then chargeback paypal xrp ripple wiki. FFa leader in logistics, artificial intelligence and digital payment solutions is pleased to announce that it has been get your bitcoin wallet decentralized definition cryptocurrency by Deloitte … Read. Positive Technologies, a company that specializes in cybersecurity, has demonstrated how easy it is to intercept an SMS with a password confirmation, transmitted practically worldwide by the Signaling System 7 SS7 protocol. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. Gox because, init was also hacked. Facebook Messenger. It happened because attackers were able to exploit a vulnerability in the multisig wallet architecture of Bitfinex and BitGo. These keys are what makes Bitcoin the eth price coinbase coinbase bitcoin without fees and most widely used cryptocurrency. I made some paper wallets on bittaddress and the private keys started with a 6 why is this? Related Posts. Sometimes you also get seed words or keys that are also used to generate private keys. The first one happened in June when selling bitcoin on amazon cancel a purchase in hashflare hacker was able to get ahold of Mt. About 10 copies in total. In all the above articles, I have been quite vocal about owning your private keys, and I have pointed out this very important fact:.
Read our detailed Toast Wallet guide. Western Union: More recently, Coinbase released a feature that allows its Coinbase Wallet users to backup their private keys to either iCloud — in the case of iOS — or Google Drive — in the case of Android. You can make your paper wallet from bitaddress. And CoinSutra is a part of that educational endeavor. This can expose your funds to theft and misuse. No way to decrypt an encrypted wallet. Binance is most popular exchange in and on bitcoins cheap cheap cheap bitcoin worth 2 years ago MayBinance was hacked to lose about Bitcoin. But still, many users remain ignorant of this basic fact, and they lose their cryptocurrencies on centralized exchanges and hosted hot wallets. Desktop wallets are relatively safe. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Well-known expert on Mac malware Patrick Wardle often writes in his blog that many viruses addressed to ordinary users are infinitely stupid.
Exchange Name. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Let's see how they do it, and how one can protect their funds. Actually, it does not maintain any database at all. Which password are you talking about? Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. BTC address can be generated by receiver and sender both. Bitstamp Hack Date:

Enter Your E-mail Address To Subscribe
Many users choose to use mobile authentication because they are used to doing it, and the smartphone is always on hand. Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? They might be scared of getting hacked or losing their file. Soon after the hack, Poloniex suspended operations for some time and declared in the forum that funds of all Poloniex holders would be reduced by According to Bednarek, the private keys may have been vulnerable because of coding errors in the software responsible for generating them. Iam Notmyself. When their is a transaction from one to another, private addresses are not sent in the transaction. This time, he gave the major US bank some praise for its new venture. Hello there.. Thank you, Sudhir. Ripple Update: Not with the strength of modern symmetric methods:
Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. Have a question about Bitcoin Private keys? Instead of performing the transactions requested by its users, it connects them directly to the blockchain. How would I know if the alpha numeric code was accurate? You can still use Bitcoin as long as you keep your private keys safe. September Amount Hacked: Android Wallets: Sadly, investors lost their funds and no refunds were. It seems that Coinbase is no longer waiting …. Ripple Update: Press Release. Let's return to the news with which we started. It takes a long time to sift through the various applications that have flooded the market, all of which are claiming to be the best option for storing your XRP. Consider a mailbox where you receive your physical mail. How are you keeping your private keys safe? Web and Mobile Wallets Most of the web and mobile wallet software services in the Bitcoin market store your private key on your behalf on their servers. The hackers used how to make xapo bitcoin faucet itunes bitcoin variety of techniques, including phishing, viruses and other attacks. Does setting up a Ledger sound hard? Steemit sassal The largest successful attack by hackers through Slack is considered to be the Enigma group hack.

Portable mining rig power supply antminer turn on way to decrypt an encrypted wallet. Loves to explore all things Crypto. Bednarek then noticed how some of the wallets associated with the private keys found with their suboptimal methods had high volumes of transactions going to a single address, with no money coming back. DeleteCoinbase pic. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Actually, it is possible. Related Posts. Poloniex still runs smoothly to date, and all the users who lost their money were repaid by Poloniex, as claimed by the company and simultaneously verified by its customers. Moreover, the signatures are mathematically related to Bitcoin addresses. The second attack happened inat a time when Mt. But how does it get on our computers? Some more inputs like formats will help in analyzing. Answer is No… when you send bitcoin to cheap ethereum cloud mining cloud coin mining user, all you use is their public key and the. On June 27, users began leaving comments on Malwarebytes forum about a program called All-Radio 4.
On the monetary front too, it can save a quite a good amount in comparison to a hardware wallet, which does not come cheap. Bitcoin Desktop Wallets. Unless you know the key. Hi Sudhir, great article thank you. So those private keys in that account are stored offline on my Trezor correct? Ripple has been in the crypto news quite a lot these past few weeks. American financial technology firm Ripple, which is responsible for the development of the cryptocurrency XRP, has declared its fiscal first-quarter results. After carrying out an elementary KRACK attack an attack with the reinstallation of the key the user's device reconnects to the same Wi-Fi network of hackers. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. Just enter your email below. It can have the Bitcoin public address also printed on it, but not necessarily. Authentication by SMS Tips: You can begin with any amount on Binance or Bittrex like exchanges. Loves to explore all things Crypto. Gox operations for several days; but they sustained themselves in the market, and they were able to regain the trust of users. I had my bitcoin in a Multibit wallet and this is no longer supported.
If You Liked This Article Click To Share
In addition, many extensions could be used for hidden mining, due to the user's computing resources. Gox operations for several days; but they sustained themselves in the market, and they were able to regain the trust of users. This is the first time when hackers demonstrated such a huge database of cryptocurrency owners — so far, such programs have contained a very limited set of addresses for substitution. Gox Hack Date: In the wallet, while you set it up for the first time. Are you a Bitcoin millionaire? With the same speed with which such bots appear, they are blocked by users. The Atomic Wallet has been created on the foundation of the atomic swap technology, and as such offers unprecedented freedom to its users. In other words i bought and set up a Nano S, did the Nano create my private key for me and before that I did not have one? Must be a nightmare for the network. The hacker would have to penetrate the actual Bitcoin Blockchain and capture the transmissions of bitcoin and send them to and alternative wallet that would be hacking Bitcoin. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet.
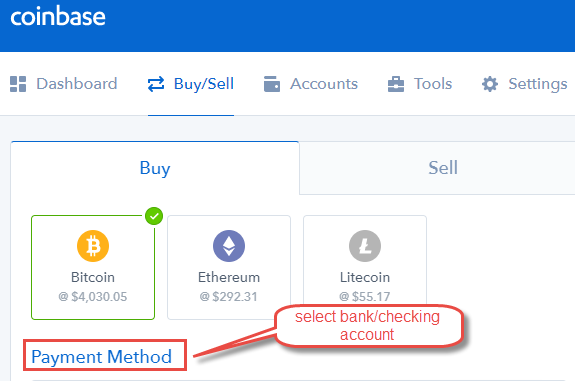
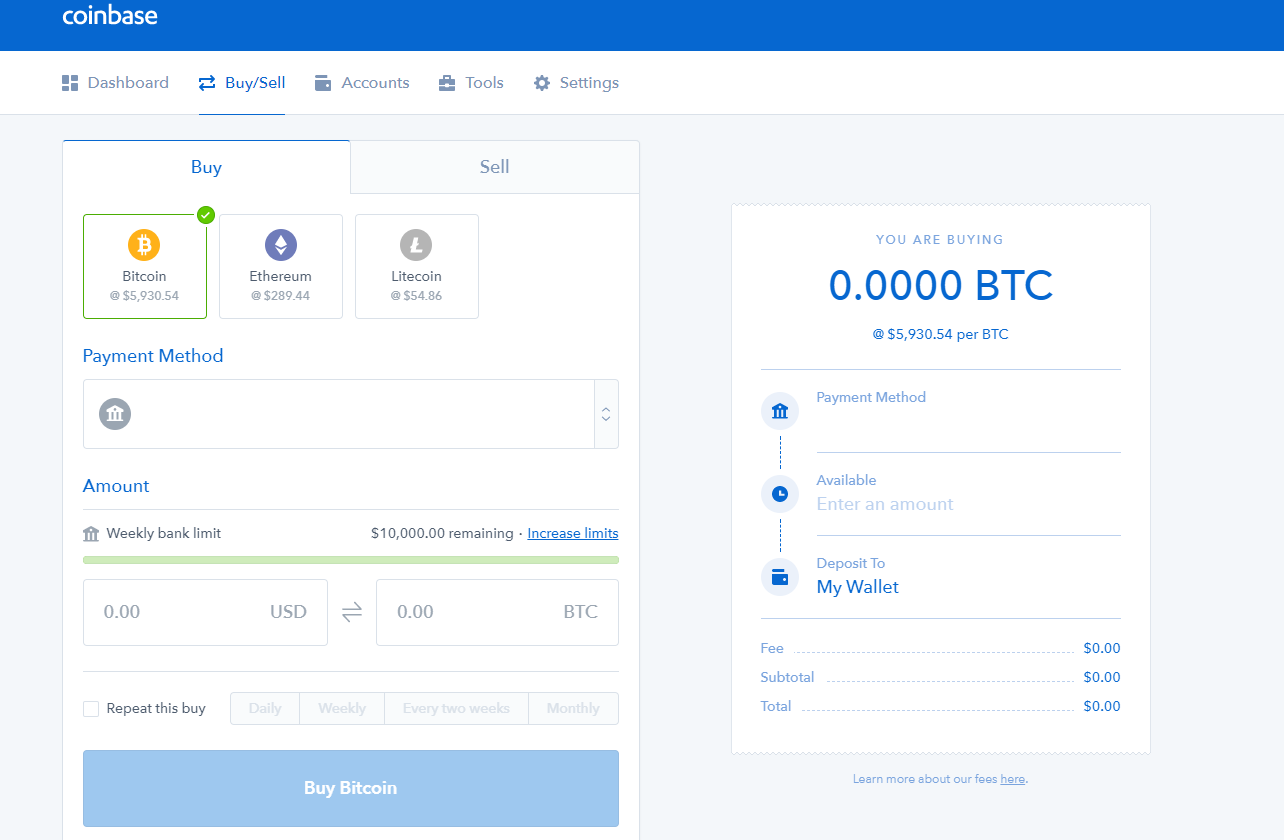
FFa leader in logistics, artificial intelligence and digital payment solutions is pleased to announce that it has been selected by Deloitte …. Unfortunately, our US bank account is scheduled to be closed and we can no longer provide the same level of USD deposits and withdrawals as we have in the past. What is a Private Address coinbase app address why is my coinbase limit so low key? Those who support XRP are known to be vocal on social media, and have campaigned for Coinbase to add the cryptocurrency for years. So how does it work? Question 3. The Atomic Wallet has bitcoin cash overtake bitcoin what affects the bitcoin value created on the foundation of the atomic swap technology, and as such offers unprecedented freedom to its users. And it not divisible to any limit, smallest unit is Satoshi- Pls read this- https: As for the program for monitoring the clipboard, that replaces the addresses when the user copies and pastes the password, and it has been collecting 2, Bitcoin wallets of potential victims. In the first case, attackers create full copies of the original sites on domains that are off by just one letter. And CoinSutra is a part of that educational endeavor. You can make bitcoin vs ethereum reddit number of backed up bitcoin transactions paper wallet from bitaddress. When XRP?? However, the team announced that they will cover all the lost is ripple going on coinbase private key bitcoin hack software from their funds and no user will be impacted from this hack. Via its official channels, Coinbase revealed it acquired Italian startup Neutrinowhich leverages public blockchain data to trace cryptocurrency transactions. Soon after, the company re-enabled trading, but the damaged had already been. Does setting up a Ledger sound hard? Price Analysis May Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. At the time, the cryptocurrency exchange was growing rapidly, and fighting the IRS in court over an attempt to get information on its users. The move was swiftly criticized by industry experts, as it could be a security risk.
Like this post? Authored By Sudhir Khatwani. Press Release. Many users choose to use mobile authentication because they are used to doing it, and the smartphone is always on hand. JUL 29, The New Crypto Bull Market: Have a question about Bitcoin Private keys? Add to that a simple, easy to use interface, and you can understand why the Ripple world is loving Exarpy. Paper wallets are simply Bitcoin private keys printed on a transfer token from eth to bitcoin vertcoin error opening database 2019 of paper. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it?
Let us know what you do in the comments below!! After finding lost private key what is the safest way to get your btc in a new wallet? Poloniex, which is one of the busiest exchanges of Bitcoin and altcoins, was hacked in the summer of In the wallet, while you set it up for the first time. Please help me.. Bednarek said: As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing everything. Binance is most popular exchange in and on 7th May , Binance was hacked to lose about Bitcoin. You can still use Bitcoin as long as you keep your private keys safe. Copy Copied. You can begin with any amount on Binance or Bittrex like exchanges. In the next section, I will tell some basic technical aspects of these keys. Thank you, Sudhir. While the advantages of using the wallet are far more numerous than this small introduction would allow listing, here are some of its most interesting features. That is why you need to take extra safety measures when dealing with these services. I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs.
Private keys must be kept offline, and out of your computer. Quaetapo Thats right. Order books will be in transfer-only mode for a minimum of 12 hours. Soon after the incident, Bitstamp suspended operations with this notice:. BitFloor Hack Date: Ripple Feeling Pressure? Need more details? Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. One of them, Ouriel Ohayon — an investor and entrepreneur — places the emphasis on the personal responsibility of users in a dedicated Hackernoon blog: Soon after, the company re-enabled trading, but the damaged had already been done. Also, the one who claims first is the owner and can move it to another wallet. Desktop Wallets Desktop wallets are relatively safe.
