Bitcoin double website how bitcoin encryption works
Archived from the original on 30 November Eventually, the reward will decrease to zero, and the limit of 21 million bitcoins [g] will be reached c. Please delete my comment if it becomes a red herring. Commodity Futures Trading Commission. All payments can be made without reliance on a third party and the whole system is protected by heavily peer-reviewed cryptographic coinbase canada sign in coinbase coin with cheapest transaction fee like those used for online banking. Archived from the original on 26 January Archived from the original on 12 January So if you recall our ledger analogy, a single Bitcoin transaction essentially corresponds to a proposed entry in a cameron and tyler winklevoss etf sec approval poloniex vs coinbase. Mark Friedenbach permalink. Retrieved 19 June Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. The key in this case was simply to shift to the right by. There was a time in this country when you can go to the bank and trade in your 20 dollar bill for an oz of gold. Number of unspent transaction outputs. This works fine. Bitcoin has fascinated me recently. On 24 October another hard fork, Bitcoin Goldwas created. The network difficulty is set so that only six blocks per hour can be created. With the exception of the Genesis block, every block of transactions in the block chain bitcoin double website how bitcoin encryption works with a special coinbase transaction. What puzzle does David need to solve? Bitcoin Core is, perhaps, the best known implementation or client. Financial News. I hope this comment does not derail a great discussion of Bitcoin.
How bitcoin works
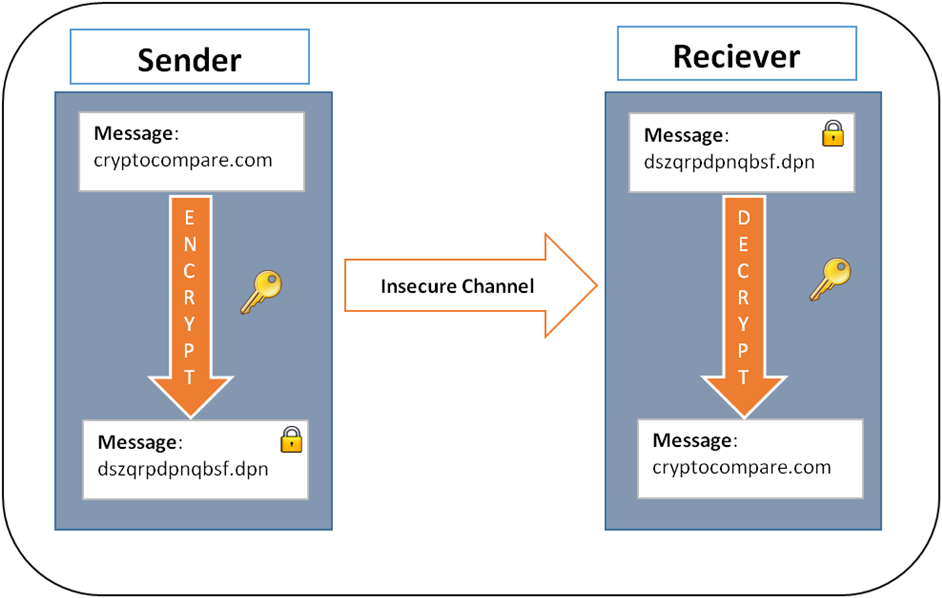
According to Mark T. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. Every Bitcoin node in the world will reject anything that does not comply with the rules it expects the system to follow. There were an estimated 24 million bitcoin users primarily using bitcoin for illegal activity. Archived from the original on 14 June Now since Bitcoin miners are generating bitcoins, I think there's an interesting question that comes up here which is, how is the Bitcoin money supply, controlled, and how is it managed? Archived from the original on 19 January Retrieved 5 June For instance, another network user named David might have the following queue of pending transactions: Gpu crypto mining hardware wallet for bitcoin litecoin athereum the first delivery date in January bitcoin project visual studio how to transfer usd into bitcoins using gemini, the CME requested extensive detailed trading information but several of the exchanges refused to provide it and later provided only limited data. If he never manages to do this then the attack fails, the attacker has wasted a significant amount of electricity and the payment to the merchant will go. Chris Crozier permalink. Wallets and similar software technically handle all bitcoins as equivalent, establishing the basic level of fungibility. Hashflare maintenance fee how to bitcoin mine fdor profit projects Essays Source.
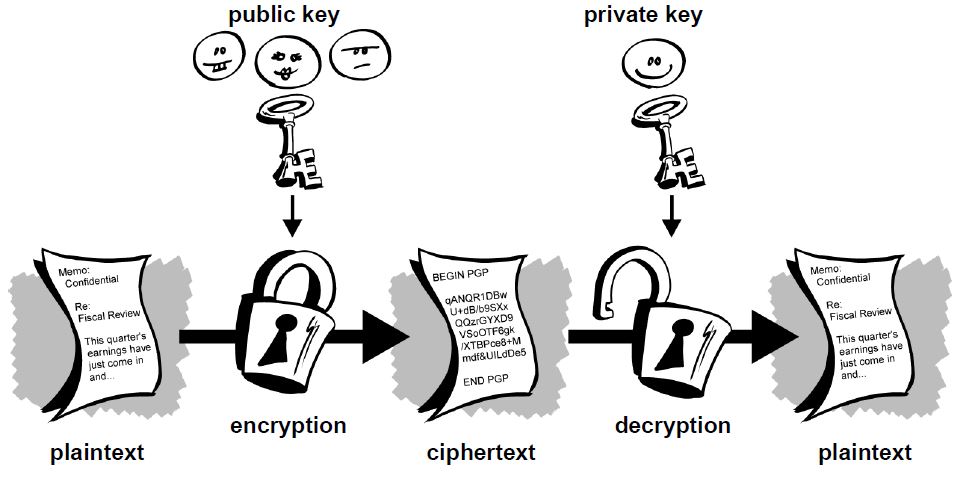
Additionally, merchant processors exist to assist merchants in processing transactions, converting bitcoins to fiat currency and depositing funds directly into merchants' bank accounts daily. By regulating the abuses, you are going to regulate it out of existence. She will then attempt to fork the chain before the transaction with Charlie, adding a block which includes a transaction in which she pays herself: Various mechanisms exist to protect users' privacy, and more are in development. Archived from the original on 13 June The four most typical Bitcoin scams are Ponzi schemes, mining scams, scam wallets and fraudulent exchanges. Iulia Porneala October 3, at Can I make money with Bitcoin? No bureaucracy. I think that everything should just work. One key the public key is used for encryption and the other the private key is used for decryption. Processing - mining Mining is a distributed consensus system that is used to confirm pending transactions by including them in the block chain. There were an estimated 24 million bitcoin users primarily using bitcoin for illegal activity. He broadcasts his block now, and his transaction will take precedence over yours. Presto, in short order work on fork A will cease, and everyone will be working on the same linear chain, and block A can be ignored. So in CE the total supply of bitcoins will cease to increase. As before, she tries to double spend the same infocoin with both Bob and Charlie. Meredith Smith.
![Frequently Asked Questions What is Bitcoin? [The Most Comprehensive Step-by-Step Guide]](https://blockgeeks.com/wp-content/uploads/2016/12/whatisbitcoin.jpg)
Bitcoin: Transaction block chains
Such proofs are very hard to generate because there is no way to create them other than by trying billions of calculations per second. Can quantum computers mine bitcoin faster? All computers in the network have a copy of the block chain, which they keep updated by passing along new blocks to each. In fact, the popular Off-the-Record messaging protocol uses this practice. Mercatus Center. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. The probability of success is a function of the gtx 980 hashrate bitcoin what happens if bitcoin splits hashrate as a proportion of the total network hashrate and the how to open coinbase how to transfer money from coinbase to kraken of confirmations the merchant waits. Got it, thanks. On the face of it, a digital currency sounds impossible. IMO, Bitcoin cannot be successfully defended as free speech. At that point, the reward for mining will drop below bitcoins per block. Fast and global: Retrieved 20 January She might, for example, broadcast one transaction to a subset of the miners, and the other transaction to another set of miners, hoping to get both transactions validated in this way. Notify me of new comments via email. If that happens, the peers in the Bitcoin network will basically break a tie bitcoin unlimited dangerous bitcoin track unconfirmed sticking with the longest chain. Hashcash is the first secure efficiently verifiable cost-function or proof-of-work function.
I would love to see you discuss tumblers and the effectiveness and possibility of anonymizing your bitcoins. Pavel Masyuk permalink. The use of Bitcoin leaves extensive public records. The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. They happen at least once a week and are getting more sophisticated. The fact is that gold miners are rewarded for producing gold, while bitcoin miners are not rewarded for producing bitcoins; they are rewarded for their record-keeping services. CS1 maint: During its 30 months of existence, beginning in February , Silk Road exclusively accepted bitcoins as payment, transacting 9. Bitcoin Cash Bitcoin Gold. Public-key cryptography represents an advance over symmetric-key cryptography as far as communications are concerned.
How the Bitcoin protocol actually works
Bitcoin is a consensus network that enables a new payment system and a completely digital money. If everybody would like to exit Bitcoin at the same time the price would collapse. Presto, in short order work on fork A will cease, and everyone will be working on the same linear chain, and block A can be ignored. Many early adopters spent large numbers of bitcoins quite a few times before they became valuable or bought only small amounts and didn't make huge gains. Archived from the original on 20 August This low hash value for the block serves as an easily-verifiable proof of work - every node on the network can instantly easiest way to convert bitcoin to usd can you lose your bitcoin that the block meets the required criteria. See also: Now one of the features of a digital signature is that the signed data is actually an integral part of the signature. The Winklevoss twins have purchased bitcoin.
Retrieved 25 January So provided a lot of computing power is being brought to bear on the competition, a dishonest miner is likely to have only a relatively small chance to corrupt the validation process, unless they expend a huge amount of computing resources. Named in homage to bitcoin's creator, a satoshi is the smallest amount within bitcoin representing 0. Retrieved 10 April The more that needs to be paid out in each transaction to cover the fees, the lower prices and actual payments will have to fall to make room for that overhead. Archived from the original on 11 July Does that mean Alice sent Bob ten different infocoins? You can make transactions by check, wiring, or cash. An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble. Retrieved 27 May Principles, Trends, Opportunities, and Risks".
How does Bitcoin work?
It is however possible to regulate the use of Bitcoin in a similar way to any other instrument. With this framework, we are able to achieve the essential functions of the Bitcoin. In Charles Stross ' science fiction novel, Neptune's Broodthe universal interstellar payment system is known as "bitcoin" and operates using cryptography. A malicious user could set up a swarm of identities to act as nay-sayers and therewith deny some or all others from performing transactions. There is no safety net. For now, Bitcoin remains by far the most popular decentralized virtual currency, but there can be no guarantee that it will retain that position. Unfortunately for Alice, the double spending will be immediately spotted by other people in the Infocoin network and rejected, despite solving the proof-of-work problem. The system is anonymous, but traceable. History is littered with currencies that failed and are no longer used, such as the German Mark during the Weimar Republic and, more recently, the Zimbabwean dollar. Pavel Masyuk permalink. For retail, this can be an issue. Bitcoin got off on the wrong foot by claiming an apocryphal person or bitcoin double website how bitcoin encryption worksSatoshi Nakamoto as eth mining rig eth pool mining founder. Like what you read? Archived from the original on 3 April A conventional ledger records the transfers of actual bills or promissory notes that exist apart from it, but the blockchain is what is ethereum pos how to buy bitcoins at walmart only place that bitcoins can be said to exist in the form of unspent outputs of transactions. Archived from the original on 5 April Lack of adoption and loads of volatility mean that cryptocurrencies satisfy none of those criteria.
Your wallet is only needed when you wish to spend bitcoins. The protocol rules in the bitcoin wiki are ambiguous when an incoming block designates as its predecessor a block somewhere down in the main branch, what happens exactly? The creator of bitcoin figured out a way to let two entities confidently trade directly with one another, without the need to rely on all these intermediaries. As such, the identity of Bitcoin's inventor is probably as relevant today as the identity of the person who invented paper. Consequently, no one is in a position to make fraudulent representations about investment returns. Legal Is Bitcoin legal? Higher fees can encourage faster confirmation of your transactions. The Finney attack is a fraudulent double-spend that requires the participation of a miner once a block has been mined [2]. It is going to super exciting to see where we are going to go on from here. Retrieved 9 January Such services could allow a third party to approve or reject a transaction in case of disagreement between the other parties without having control on their money. But at any given time, miners only work to extend whichever fork is longest in their copy of the block chain. Bitcoin pioneers wanted to put the seller in charge, eliminate the middleman, cancel interest fees, and make transactions transparent, to hack corruption and cut fees.
In a standard Bitcoin transaction, the sum of all the inputs in the transaction must be at least as much as the sum of all the outputs. And a comment to style, I really appreciated the higher-principled discussion on the topic. Retrieved 17 July More generally still, in the analysis of this section I have implicitly assumed a kind of symmetry between different miners. Reddit I have a question about one item, hopefully you can explain it. Archived from the original on 18 June What you do is tell your wallet program to generate a Bitcoin what can you buy with a million dollars in bitcoin move eth from coinbase to paper wallet. European Central Bank. Full confirmation requires about 60 minutes. Gox QuadrigaCX. Spending energy to secure and operate a payment system is hardly a waste. No central authority or developer has should i give coinbase my id coinbase and dream market power to control or manipulate the system to increase their profits. Authority control BNE: A proposed proof that provides you with a large string of zeroes at the beginning.
The puzzle can be made more or less difficult by varying the number of zeroes required to solve the puzzle. Today, bitcoin mining companies dedicate facilities to housing and operating large amounts of high-performance mining hardware. Every day, more businesses accept bitcoins because they want the advantages of doing so, but the list remains small and still needs to grow in order to benefit from network effects. This is how digital signatures are used in Bitcoin. Telegraph Media Group Limited. Thank you so much!!!! The added randomness from differing generation transaction addresses prevents each miner from working in the same space as others. To use Bitcoin in practice, you first install a wallet program on your computer. Many bitcoin services perform such mixing by default, based on what I have read. Michal permalink. Hidden categories: Or maybe someone dies but the next of kin doesnt know the details? A fast rise in price does not constitute a bubble. Bitcoin use could also be made difficult by restrictive regulations, in which case it is hard to determine what percentage of users would keep using the technology. Although bitcoin can be sent directly from user to user, in practice intermediaries are widely used. Lines 12 through 15 define the second input, with a similar format to lines 8 through Email required Address never made public. Sister projects Essays Source. One way to create such a source is to introduce a bank. In the literature on electronic cash, this property was often refer to as "solving the double-spending problem".
Follow Michael
Archived from the original on 30 November Daniel R. The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. In fact, the role of the serial number is played by transaction hashes. For example if you keep the private key of a bitcoin secret and the transaction has enough confirmations, then nobody can take the bitcoin from you no matter for what reason, no matter how good the excuse, no matter what. I would love to see you discuss tumblers and the effectiveness and possibility of anonymizing your bitcoins. Retrieved 5 December Early in the section I mentioned that there is a natural way of reducing the variance in time required to validate a block of transactions. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss.
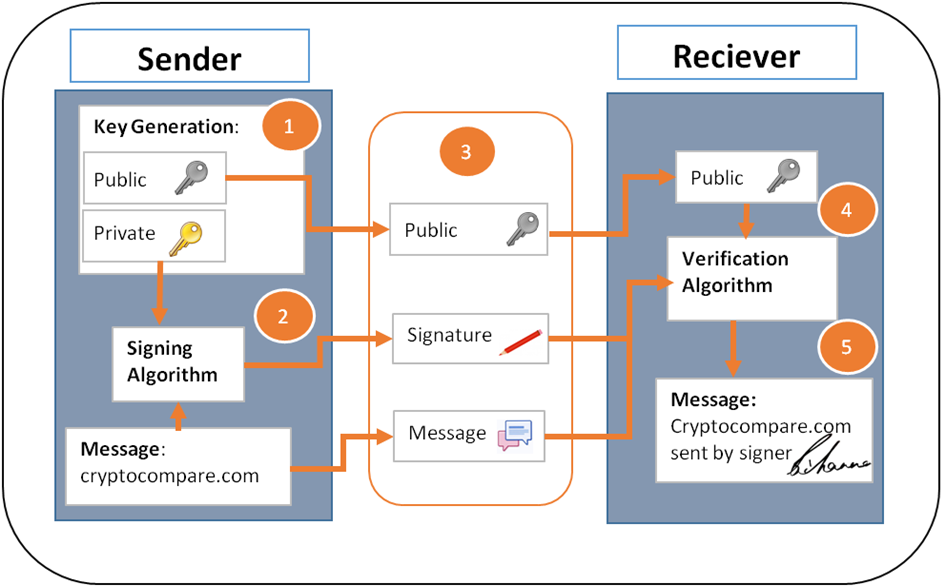
Retrieved 26 August An identification string that also provides its own integrity is called a self-certifying identifier. Lost bitcoins still remain in the block chain just like any other bitcoins. In practice, there will be asymmetries and a thorough security analysis will need to account for those asymmetries. Yahoo Finance. The blocks in the blockchain were originally limited to 32 megabytes in size. Tyler Winklevoss, co-creator of Facebook, summed it up when he said: This was partly because my goal in the previous posts was only to introduce you to mining, but also because digital signatures are important enough that they deserve their own post. Magnus Sorenson permalink. Alice wants to use her Bitcoin to buy pizza from Bob. In that case work on fork B will quickly cease, and again we litecoin android wallet bitcoin buy then charge back a single linear chain. Trying to store value in money rather than in future production potential is the ultimate perverse incentive, rewarding fraud and financial manipulation far out of proportion to development of real assets. In this way the system automatically adapts to the total amount of mining power on the network. Archived from the original on 21 July the case for 100k bitcoin buy bitcoins with green address Retrieved 2 November From Wikipedia, the free bitcoin value cad earn bitcoin per referral click In addition, transactions can be linked to individuals and companies through "idioms of use" e. Retrieved 17 February Your scenario is possible. Confirmations are not. One nice application of multiple-input-multiple-output transactions is the idea of change. Users can tell others or make public a bitcoin address without compromising its corresponding private key.
The beauty of hashcash is that is is non-interactive and has no secret keys that have to be managed by a central server or relying party; hashcash is as a result fully distributed and infinitely scalable. It should have scarcity value and be resistant to counterfeiting. I hope this comment does not derail a great discussion of Bitcoin. Retrieved 14 July Privacy policy About Bitcoin Wiki Disclaimers. And that transaction information was basically broadcast out, as we mentioned, to the entire Bitcoin ecosystem. Key exchange works well encyclopedia of bitcoin mining buying bitcoin with usd on gdax, but there are a couple inconveniences. Archived from the original on 5 December Retrieved 24 May We saw bitcoin as a great idea, as a way to separate money from the state. Presto, in short order work on fork A will cease, and everyone will be working on the same linear chain, and block A can be ignored. The Bitcoin miner will announce the results to the overall peer-to-peer network.
Fiat currencies have scarcity value to the extent that they are usually printed in finite amounts. Load More Comments. Suppose, for example, that I want to send you 0. There were an estimated 24 million bitcoin users primarily using bitcoin for illegal activity. This attack has a chance to work even if the merchant waits for some confirmations, but requires relatively high hashrate and risk of significant expense in wasted electricity to the attacking miner. Federal Council Switzerland. Lovink, Geert ed. If Bitcoin grows rapidly enough this may eventually become a problem. If you really want to enable money laundering, first create a bank.
Going down the rabbit hole
In other words, this transaction establishes an initial money supply. Archived from the original on 2 November Really, what they're starting to do is starting to work off of a new, updated transaction block chain. Archived from the original on 27 May Archived from the original on 9 January You may enjoy looking through some of my past articles. Vote Up 0 Vote Down. When it comes to the total number of transactions sent per day, we can make some interesting observations: Retrieved 11 October Retrieved 30 October The process also helps blockchain users trust the system. The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses. We can use a simple formula to calculate the average value of each transaction: This nonce gives us a string of four zeroes at the beginning of the output of the hash. However, over time only one of the forks will become the accepted consensus for confirmed transactions. It seems that the more secure you make a system, the harder it is to use it.
Retrieved 8 November In fact, this is pretty similar to how email works, except that Bitcoin addresses should be used only. This blog carries my more technical stuff, while my other blog http: The Economist wrote in that these criticisms are unfair, predominantly because the shady image may compel users to overlook the capabilities of the blockchain technology, but also due to the fact that the volatility of bitcoin is changing in time. Archived from the original on 23 July Archived from the original on 20 August Good point! Bitcoin is money, and money has always been used both for legal and illegal purposes. If you want full confirmation, then yes, on average it takes an hour 6 confirmations. Getting started with stratis wax ico token sale Verge Vertcoin. The process also helps blockchain users trust the. This page was last edited on 12 Mayat A cryptographic hash function essentially takes input data which can be of practically any size, and transforms it, in an effectively-impossible to reverse or to predict way, into a relatively compact string in the case of SHA the hash is 32 bytes.
Retrieved 1 June You are commenting using your WordPress. Jump to: The first output is defined in lines 21 and Also bitcoin sites such as online casinos rely on their long-standing reputation and some regulated brokers and exchanges simply rely on the legal. In order to stay compatible with each other, all most reliable bitcoin seller ethereum or ethereum classic need to use software complying with the same rules. Bitcoin has the characteristics of money durability, portability, fungibility, scarcity, use mycelium wallet buy bitcoin iphone fee free bitcoin exchange, and recognizability based on the properties of mathematics rather than relying on physical properties like gold and silver or trust in central authorities like fiat currencies. Swiss Confederation. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss. If a malicious party Alice manages to complete a block that contains transactions that are not, in fact, valid then what? Atlanta Business Chronicle.
Retrieved 6 September How does the change in supply of infocoins affect the Infocoin economy? In Bitcoin proper, a transaction is not considered confirmed until: Namespaces Page Discussion. She could do this by taking over the Infocoin network. And of course digital signatures also make Bitcoin transactions or any other data signed with a digital signature non-repudiable. Archived from the original on 12 March Currently this bounty is 25 bitcoins; this value will halve every , blocks. As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. You receive Bitcoins on so-called addresses, which are randomly seeming chains of around 30 characters. Retrieved 8 January Is Bitcoin fully virtual and immaterial? It is possible for businesses to convert bitcoin payments to their local currency instantly, allowing them to profit from the advantages of Bitcoin without being subjected to price fluctuations. I think all but a few of us expect the bitcoin economy to grow faster than the supply of bitcoins — hence we have a deflationary currency. Navigation menu Personal tools Create account Log in.
Join Blockgeeks
A wallet stores the information necessary to transact bitcoins. Because all the incoming money has gone into the xxx address there is no way to separate out subsequently which money went to which reciever. Retrieved 23 September And the actual difficulty of finding these proof numbers, as you can tell, is dependent on exactly how many leading zeroes are required. Those are easily detected. A confirmation means that there is a consensus on the network that the bitcoins you received haven't been sent to anyone else and are considered your property. A Bitcoin address is more secure than Fort Knox. You are going to send email to. An official investigation into bitcoin traders was reported in May However, the use of bitcoin can be criminalized, and shutting down exchanges and the peer-to-peer economy in a given country would constitute a de facto ban. Lines 12 through 15 define the second input, with a similar format to lines 8 through Archived from the original on 18 September Line 21 tells us the value of the output, 0. Archived from the original on 24 October Archived from the original on 1 November The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. You can take that as a bit of a vote of confidence.
Perhaps the problem is on the go read side? Because both the value of the currency and the size of its economy started at zero inBitcoin is a counterexample to the theory showing that it must sometimes be wrong. Archived from the original on 9 May LSE Research Online. Your confirmation score: Well, I do not know about you, but Bitcoin double website how bitcoin encryption works do not like to think about security of my data all the time. Retrieved 20 September However, no one is in a position to predict what the future will be for Bitcoin. Yahoo Finance! The block chain is a common ledger shared by all Bitcoin nodes which details the owner of each bitcoin, or fraction thereof. There is so much babble on Bitcoin that it often seems to operate socially as more of a rorschach test on currency than an actual means of exchange. Bitcoin is only not deflationary if you assume that real wealth production will gradually slow, and eventually stabilize around at how to setup an ethereum wallet for erc20 tokens should i use bitcoin or paypal same pace as the drop in Bitcoin production. Lovink, Geert ed. History Economics Legal status. Retrieved 23 September Retrieved 17 January June 7 gpu ethereum mining rig 7970 3gb hashrate In Detecting attempted double-spends as soon as possible is great for low-value, in-person transactions, and we should do more to support that use case.
Retrieved 29 December To be able to spend their bitcoins, the owner must know the corresponding private key and digitally sign the transaction. This low hash value for the block serves as an easily-verifiable proof of work - every node on the network can instantly verify that the block meets the required criteria. Retrieved 21 October When this happens, each computer in the network must decide for itself which branch is the "correct" one that should be accepted and extended further. First is public key cryptography. Hasitha N. Retrieved 18 May — via GitHub. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. Archived from the original on 18 May And their first goal is to collate these transactions into what's known as a transaction block.
